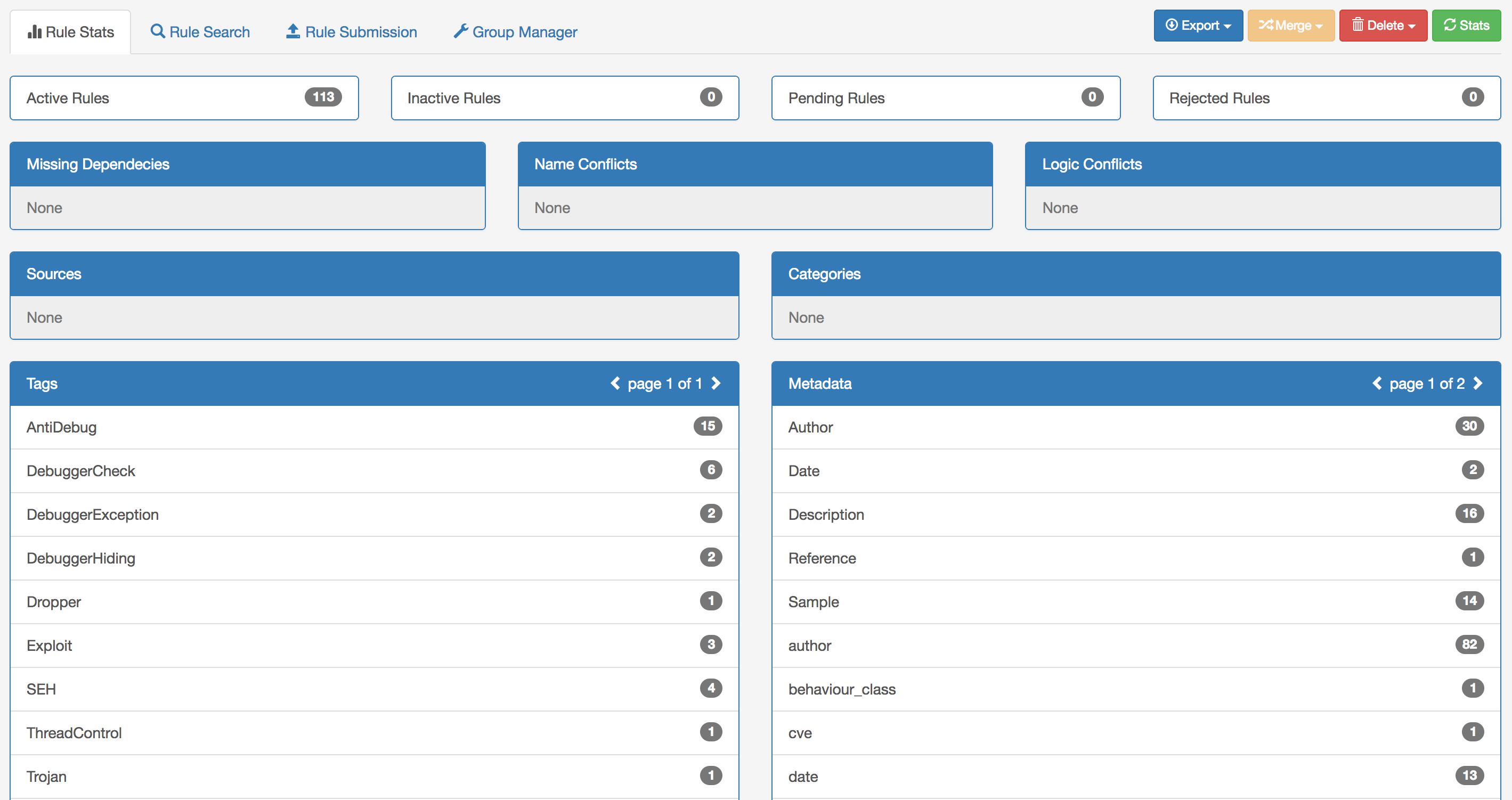
CrowdResponse:
is a community-based platform that may
eventually support as many as 25 software modules, each serving a
different aspect of the incident response process, Kurtz says. This
week's release includes three modules: @dirtlist, @pslist, and @yara.
@dirlist
This is the directory-listing module. This sounds quite simple, but it is actually extremely powerful.
The
CrowdResponse DirList module enables the following features:
- Verify and display digital signature information
- Utilize a path exclusion/inclusion regular expression filter that acts on the full path name
- Use a file wildcard mask to limit processing to specific file name components
- SHA256 and MD5 file hashing
- Perform "quick" hash of only the first 512 bytes of the file
- Option to not hash files greater than a given size
- Display application resource information
- Select recursive listings and control recursion depth
- Display creation, modification and access times for files
- Optionally process only Windows executable (PE) files
@pslist
This is the active running process listing module.
The
CrowdResponse PSList module enables the following features:
- Verify the digital signature of the process executable
- Obtain process command line
- Obtain detailed PE file information for each process executable
- Perform SHA256 and MD5 hashes of process executables
- Enumerate loaded modules for each process
- Control PE output detail level of function names for imports and exports
- Control PE output detail level of resource information
- Control format (nested or flat) for PE file resource information
- Check for process thread injection
@yara
The
YARA processing module is the one I am most excited about. YARA will be
familiar to many as an incredibly useful tool aimed at helping malware
researchers identify and classify malware. It can act on files on disk
or in-memory process images and runs a set of pattern matching rules
against the target of investigation.
While we have incorporated a fully functional version of YARA into
CrowdResponse,
we have made it very simple to use for analyzing all active process
binaries and memory. Along with the regular ability to target a specific
single-process ID or one or more files, we can automatically enumerate
all running processes and launch YARA rules against them all by simply
specifying a single tool option. This enables quick and easy evaluation
of a system without resorting to cumbersome scripting. This
functionality greatly speeds the scan time and aids a responder in
quickly pinpointing adversary activity on a suspect system.
The
CrowdResponse YARA module enables the following features:
- Scan memory of all currently active running processes
- Scan on-disk files of all currently active running processes
- Download YARA rule files from a provided URL
- Control target path recursion depth
- Utilize a target path exclusion/inclusion regular expression filter that acts on the full path name
- Use a file target wildcard mask to limit processing to specific file name components
- Option to only show positive hits
- Option to specify YARA rule file name mask
- Utilize a YARA file inclusion regular expression filter that acts on the full path name
- Scan all loaded module files of active processes
- Operate on a single process ID
- Optional recursion into provided YARA rules directory
Crowd Response is a lightweight Windows console
application designed to aid in the gathering of system information for
incident response and security engagements. The application contains
numerous modules, each of them invoked by providing specific command
line parameters to the main application. Modules are all built into the
main application in C++ language utilizing the Win32 API to achieve
their functionality.
Crowd Response results may be viewed in a variety of ways,
particularly when leveraging CrowdStrike’s CRconvert. By default, output
from Crowd Response is provided in an XML file. CRconvert will flatten
this XML to CSV, TSV or HTML, if desired. The various format options
were created to support the different needs and analysis preferences of
the end user.
Supported Operating Systems: The tool runs on 32 bit and 64 bit versions of Windows from XP and above.
Download Link :
Click Here
-
MD5 87b58fb3da849cedff3a107bfe600e9b
-
SHA1 08e5bed8e7ba7316e6ff23610561b14057a58d4c
-
SHA256 c5ab1006f47bba30fe23bccf9eebedf824efa3bc6212989c748aa147221b5103