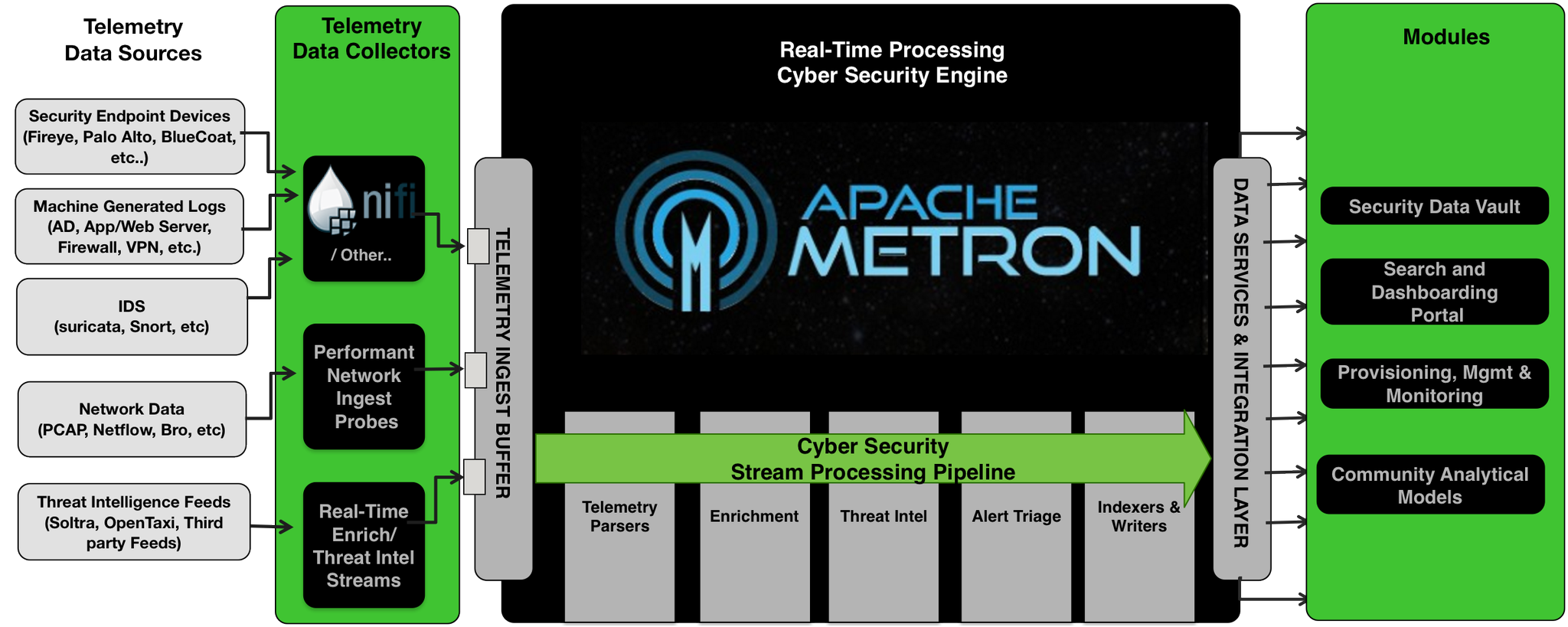
SIEMonster Security Information and Event Management (SIEM):
built on customizable, components. Included is UEBA, Bro, Suricata, The Hive, Cortex, Apache Ni-Fi, Kafka, MISP and Wazuh.SIEMonster provides Community Edition is a single appliance or Virtual machine, for companies from 1-100 endpoints. It is completely free to use.
SIEMonster is a collection of the best open source security tools and our own development as professional hackers to provide a SIEM for everyone. We showcase the latest and greatest tools for security professionals and our Community Edition v.4 Fully Loaded has it all. Designed for smaller organizations, charities, classrooms or even those who just want to check out our Fully Loaded SIEM. This edition is completely free, for the community and to be supported by the community.
Community Edition gives you the ability to monitor all network assets in an affordable scalable solution. This single server solution makes it easier for organizations who only have 1-100 endpoints. To access the Community Edition you will need to sign up to the Community Portal, which is available via the download button on our website. There you will also find all the resources you will need to help install and learn about SIEMonster. We have created an admin guide and videos for you. You are also encouraged to interact with other Community Edition users for support or just share how you are using the SIEM and even help out another user, after all that’s what Community is all about.
SIEMonster’s slogan is SIEM for everyone and this is why our prices are so affordable. Whether you are a small, medium or large enterprise we have the right product and licensing for you.
Pre Requisites :
You will need a minimum of 32GB RAM and 8 VCPU’s of power.
Note: Community edition will monitor up to 100 endpoints at 5,000 EPS as it’s designed to give you a taste and allow you to play with the product for as long as you like.
When you’re ready to get serious, let us know, and we’ll help you with our other editions.
Reference : Docs | Videos
https://siemonster.knowledgeowl.com/help
Download Link:
https://go.siemonster.com/Community-Edition